A peep into Internet World: Security Issues
Corporations of various domains like banking and finance, software engineering, stock market and trading, online shopping, media and entertainment, ecommerce have been computerized and they need Internet connection to control their network.
When a network (let it be LAN, WAN or MAN) is connected to Internet, it is implicit that the system is prone to information theft and security becomes an issue overall. Internet allows internetworking between LANs and WANs enabling remote access and control over the network from remote location. Refer (To see Figure Internet users and Firewall Security) to observe how firewall works in a network.
Anybody can hack your information when the sensitive data traverses across the network, which fuels hacking, cybercrimes and information theft. Data loss is very expensive that it is becoming unbearable to a huge extent at times of business collapse. Preventive measures is on the road to secure information and a new method “Firewall” was established to control network traffic and ‘filtrate’ unauthorized access to interfere into your network. With wan firewall, our hardware drives and files kept away from virus attacks and restrictions for users allowing only authorized users to access and gain control over your network.
Why do we opt for Firewall?
In general, firewall performs ‘filtration’ by eliminating unauthorized entries and avoids virus flow into network as a preventive action. Other options provided for security are:
- Password encryption
- Fingerprint identification
- Digital Signatures
- PIC (Personal Identification Code)
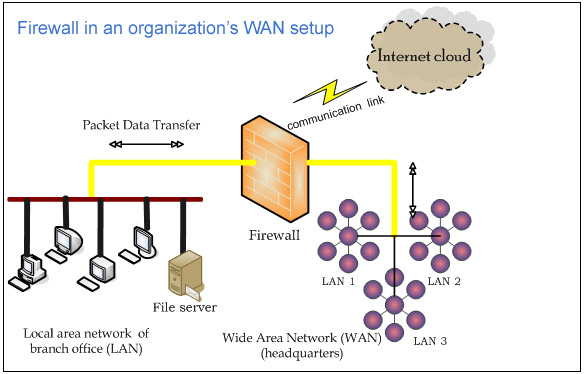
Scenario of Single Firewall:
In general, WAN setup in an organization possesses a single firewall to filtrate unauthorized entries by forming two-network structure: external and internal network. Such networks consist three interface layers with respect to ‘De Militarized Zone’ and ISP (Internet Service Provider).
Interface Layers:
- Layer 1: The external network of the organization connects with ISP on this network layer. (first interface)
- Layer 2: The internal network forms the next network layer. (second interface)
- Layer 3: The DMZ zone forms the last network layer forming last network layer.(third interface)
In a communication network, a single firewall handles entire filtration process and controls the Internet traffic between the above-mentioned layers using the implementation of traffic management techniques. Refer (To see Figure Firewall in an organization’s WAN setup) for a firewall implementation in an organization’s network.
With the existence of a single firewall, the entire internet traffic takes place between DMZ, external and internal network making it risky as at any point of time the network fails to function (artificial or manmade activities). This scenario necessitates the need of firewall in multiple WANs.
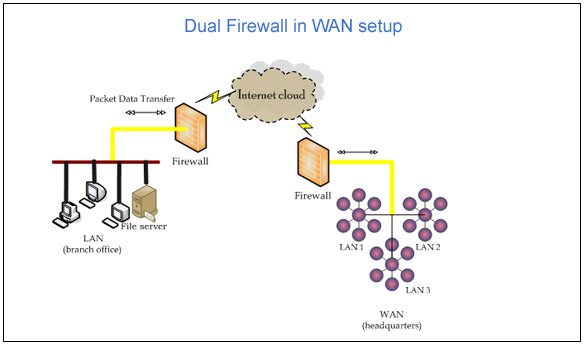
As a preventive act, experts suggest an alternate approach of implementing ‘double firewall’ or ‘dual firewall’ to segregate Internet traffic between the two network layers towards DMZ zone. This is more secure and reduces ‘traffic overload’ and traffic management is on a better scale.
Dual WAN is enabled by connections from two different ISPs connected to their WAN modems (cable modem or DSL type). With the existence of two or multiple connections user can stay connected to internet and each connection acquires a firewall ensuring reliability and security over data transfer and bandwidth optimization (bandwidth increases with multiple internet connections and dual link internetwork modem to ISP connections via two WAN ports)
Configuration:
Configuration of wan firewall is of two types based on their operations:
- Front-end firewall: Configuration done in first firewall, termed as ‘primary’ as it is intended to handle traffic for ‘De Militarized Zone’ alone.
- Back-end firewall: Configuration done in second firewall, termed as ‘secondary’ between DMZ and internal network. Traffic management handled for DMZ and internal network.
On comparison, front-end firewall has to manage heavy traffic (as they are located in such a way they handle traffic for DMZ traffic) than back-end firewall that is self-explanatory. Refer (To see Figure Dual Firewall in WAN setup) for dual firewall in a network setup.
Firewall Recommendations:
In a network, it is better to use dual firewalls each from different vendors. This becomes effective only when a hacker tries to shatter the primary firewall, the latter firewall can still proceed to work, as it is a tedious task to get through the second firewall. It is highly ‘dangerous’ to fix double wan firewalls from same vendor.
This is a backup activity to handle disasters and attain business process continuity with wide area network optimization and traffic management techniques by implementing two firewalls in a wide area network setup of an organization at an affordable cost (not expensive as to a loss in a business collapse). This is also termed as ‘firewall failover’ as it acts as a ‘backup factor’ over the collapse of first firewall.
Benefits of Dual WAN Firewall:
- Business security: Business organizations having dual wan firewall avail full benefits by boost up the security level thereby enhancing the network security by protecting the dual wan network with dual firewall
- Network Computing: use SPI process (Stateful Packet Inspection) that inspects every packet crossing in its network under its control that safeguards network computations.
- Network Security: To achieve network security, packet data that traverse across network has to undergo two major transformations: encryption and decryption. At the sender side, packet is encrypted using various algorithms like triple DES (Data Encryption Standard), AES(Advanced Encryption Standard) using a key to encrypt and pass the ciphered data to destination. At the receiver end, decryption takes place with a match key of the source to reveal original data, thus maintaining privacy using authentication process.
- Dual WAN ports: A dual wide area network gigabit router has six ports of which two WAN ports possess 10/100 megabits per second ISP connections (Mbps) and four LAN ports of gigabit power used to connect as a secondary link to the second ISP connection. Such ports enable dual wan gigabit router to handle ‘internet load balancing’
- Unified Bandwidth Management: Gigabit power (equals one megabyte of computer information) is suitable for critical networks consuming high bandwidth increasing throughput. UBM is very efficient with FatPipe product ‘QoS’ that guarantees ‘correct bandwidth for mission critical applications’, ‘allocating bandwidth thus reducing bandwidth requirements’ as a whole.
- Quality of Service: As the name entails, QoS involves analysis of what kind of service received from the internet service provider. In general, QoS provides same level of bandwidth allocation to all applications with no bandwidth priorities, leading to over provisioning thus making it ineffective. FatPipe QoS device allocates highest priority for mission critical applications and proceed with ten priority levels’
- Traffic Optimization: IP network traffic comes under control by prioritization and bandwidth provisioning that is termed as traffic optimization techniques. IP traffic passing through FatPipe QoS undergoes ten priority levels giving granular control over application and associated bandwidth with traffic load balancing to control, shape and optimize real time traffic and maximize utilization of all wan links.
- Wide Area Network High Availability: Dual WAN setup ensures high level connectivity to ISP and acts as a load balancer managing IP traffic and bandwidth allocation showing high reliability and efficiency with high grade performance as it the best preventive act for disasters and manmade failures.
Thus with two wide area network firewall, any organization can gain full control and access to Internet meeting daily requirements and transactions done with tight security by blocking hackers entry into a network and curb their access to private business data with permission restriction. A dual wan setup assures you with firewall failover, automatic failover and maintains your network status always ‘UP’!
Today’s business world entirely depends on dual factors that are ‘vital’ for any business. One is technology, which uplifts the trade to a higher range and other is modes of communication for information exchange assisted with data transfer. These serve as crucial factors at any cost, which can very well determine the lifespan of business sector.
Looking deep into the first factor, the organizations’ network should be completely equipped with most appropriate technology (tuning with operational environment) in such a way that their network withstands any disaster making the company prolong on the track of progress amidst tough competitions in market.
Why do organizations need Dual-WAN?
Most of the corporate companies work in multiple locations (let it be local, regional, national and international branches) thus expanding their networks where maintenance of huge networks becomes a massive task to perform. Due to the evolution of Internet in business, communication turned to be simpler and business operations have become trouble-free. Using internet, organizations can form a WAN (Wide Area Network) with shared users irrespective of geographical location. Therefore, business via Internet has become beneficiary on a large scale.
Let us see an example to illustrate the necessity of ‘dual wan’. Assume company X has its LAN interconnected with its scattered branches through Internet or WAN links. This is possible with single ISP (Internet Service Provider) connection, which is a usual scenario.
When the LAN has access to WAN, security over transactions and data protection becomes a question (?) as they are prone to danger due to exposure and anyone can hack the data and information theft can be done on a large scale which may lead to network failure. It is highly unaffordable to bear the loss of communication and information theft.
Is Dual-WAN obligatory?
Sudden crisis arise when network is jammed with IP traffic and users post multiple requests at the same time slice. There is no assurance that the single ISP connection will work always. In such cases ‘Dual WAN’ effectively turns to be the best measure to overcome failures with affordable cost.
As the name implies, Dual-WAN refers to the network encompassing two internet / widea area network connections using one or more routers to work. Dual-WAN links connects your networks via two separate modems or routers (cable modem or DSL modem) for dual ISP connections. Here WAN modem M1 stays in ‘active’ state and WAN modem M2 takes over the operations only when M1 fails. The purpose of Dual WAN is effective and efficient in current scenario and the reason is self-explanatory.
What is so special about two wide area network links?
Two WAN or Internet links related technological complete details are put forth with several striking features of which few require significance to mention:
- Automatic failover
- Redundancy with Dual WAN links
- Virtual Private Network
- Increased security
- Load balancing
- Firewall like functionalities
- Traffic Optimization & Acceleration
- Unified Bandwidth Management
- Business Process Continuity & Disaster Recovery
1 comment:
Great Article. Thank you for sharing! Really an awesome post for every one.
Secrecy Performance Analysis of Analog Cooperative Beam forming in Three Dimensional Gaussian Distributed Wireless Sensor Networks Project For CSE
Security Aware Cross Layer Resource Allocation for Heterogeneous Wireless Networks Project For CSE
The Security Reliability Tradeoff of Multiuser Scheduling Aided Energy Harvesting Cognitive Radio Networks Project For CSE
Trust Assessment in Vehicular Social Network based on Three Valued Subjective Logic Project For CSE
Optimizing Gradual SDN Upgrade sin ISP Networks Project For CSE
PETASCALE A Scalable Buffer lessAll optical Network for Cloud Computing Data Center Project For CSE
Traffic Load Balancing Using Software Defined Networking (SDN) Controller as Virtualized Network Function Project For CSE
Visualize Your IP Over Optical Network in Real timeA P4 Based Flexible Multilayer In Band Network Telemetry (ML INT) System Project For CSE
Post a Comment