Data Integrity
This is the function that verifies the characteristics of a document and a transaction. Characteristics of both are inspected and confirmed for content and correct authorization. Data Integrity is achieved with electronic cryptography that assigns a unique identity to data like a fingerprint. Any attempt to change this identity signals the change and flags any tampering.
Authentication
This inspects, then confirms, the proper identity of people involved in a transaction of data or value. In authentication systems, authentication is measured by assessing the mechanisms strength and how many factors are used to confirm the identity. In a PKI system a Digital Signature verifies data at its origination by producing an identity that can be mutually verified by all parties involved in the transaction. A cryptographic hash algorithm produces a Digital Signature.
Non-Repudiation
This eliminates the possibility of a transaction being repudiated, or invalidated by incorporating a Digital Signature that a third party can verify as correct. Similar in concept to registered mail, the recipient of data re-hashes it, verifies the Digital Signature, and compares the two to see that they match.
Authorization and Delegation
Authorization is the processes of allowing access to specific data within a system. Delegation is the utilization of a third party to manage and certify each of the users of your system. (Certificate Authorities).

Auditing and Logging
This is the independent examination and recording of records and activities to ensure compliance with established controls, policy, and operational procedures, and to recommend any indicated changes in controls, policy, or procedures.
Management
Is the oversight and design of the elements and mechanisms discussed above and below. Card management also requires the management of card issuance, replacement and retirement as well as polices that govern a system.
Cryptography / Confidentiality
Confidentiality is the use of encryption to protect information from unauthorized disclosure. Plain text is turned into cipher text via an algorithm, then decrypted back into plain text using the same method.
Cryptography is the method of converting data from a human readable form to a modified form, and then back to its original readable form, to make unauthorized access difficult. Cryptography is used in the following ways:
- Ensure data privacy, by encrypting data
- Ensures data integrity, by recognizing if data has been manipulated in an unauthorized way
- Ensures data uniqueness by checking that data is "original", and not a "copy" of the "original". The sender attaches a unique identifier to the "original" data. This unique identifier is then checked by the receiver of the data.
The original data may be in a human-readable form, such as a text file, or it may be in a computer-readable form, such as a database, spreadsheet or graphics file. The original data is called unencrypted data or plain text.The modified data is called encrypted data or cipher text. The process of converting the unencrypted data is called encryption. The process of converting encrypted data to unencrypted data is called decryption.
Data Security Mechanisms and their Respective Algorithms

In order to convert the data, you need to have an encryption algorithm and a key. If the same key is used for both encryption and decryption that key is called a secret key and the algorithm is called a symmetric algorithm. The most well-known symmetric algorithm is DES (Data Encryption Standard).

The Data Encryption Standard (DES) was invented by the IBM Corporation in the 1970's. During the process of becoming a standard algorithm, it was modified according to recommendations from the National Security Agency (NSA). The algorithm has been studied by cryptographers for nearly 20 years. During this time, no methods have been published that describe a way to break the algorithm, except for brute-force techniques. DES has a 56-bit key, which offers 256 or 7 x 1016 possible variations. There are a very small numbers of weak keys, but it is easy to test for these keys and they are easy to avoid.
Triple-DES is a method of using DES to provide additional security. Triple-DES can be done with two or with three keys. Since the algorithm performs an encrypt-decrypt-encrypt sequence, this is sometimes called the EDE mode. This diagram shows Triple-DES three-key mode used for encryption:

If different keys are used for encryption and decryption, the algorithm is called an asymmetric algorithm. The most well-known asymmetric algorithm is RSA, named after its three inventors (Rivest, Shamir, and Adleman). This algorithm uses two keys, called the private key. These keys are mathematically linked. Here is a diagram that illustrates an asymmetric algorithm:

Asymmetric algorithms involve extremely complex mathematics typically involving the factoring of large prime numbers. Asymmetric algorithms are typically stronger than a short key length symmetric algorithm. But because of their complexity they are used in signing a message or a certificate. They not ordinarily used for data transmission encryption.
As the card issuer, you must define all of the parameters for card and data security. There are two methods of using cards for data system security, host-based and card-based. The safest systems employ both methodologies.
Host-Based System Security
A host-based system treats a card as a simple data carrier. Because of this, straight memory cards can be used very cost-effectively for many systems. All protection of the data is done from the host computer. The card data may be encrypted but the transmission to the host can be vulnerable to attack. A common method of increasing the security is to write in the clear (not encrypted) a key that usually contains a date and/or time along with a secret reference to a set of keys on the host. Each time the card is re-written the host can write a reference to the keys. This way each transmission is different. But parts of the keys are in the clear for hackers to analyze. This security can be increased by the use of smart memory cards that employ a password mechanism to prevent unauthorized reading of the data. Unfortunately the passwords can be sniffed in the clear. Access is then possible to the main memory. These methodologies are often used when a network can batch up the data regularly and compare values and card usage and generate a problem card list.
Card-Based System Security
These systems are typically microprocessor based cards. A card, or token-based system treats a card as an active computing device. The Interaction between the host and the card can be a series of steps to determine if the card is authorized to be used in the system. The process also checks if the user can be identified, authenticated and if the card will present the appropriate credentials to conduct a transaction. The card itself can also demand the same from the host before proceeding with a transaction. The access to specific information in the card is controlled by (1) the card's internal Operating System and (2) the preset permissions set by the card issuer regarding the files conditions. The card can be in a standard CR80 form factor or be in a USB dongle or it could be a GSM SIM card.
Threats to Cards and Data Security
Effective security system planning takes into account the need for authorized users to access data reasonably easily, while considering the many threats that this access presents to the integrity and safety of the information. There are basic steps to follow to secure all smart card systems, regardless of type or size.
- Analysis: Types of data to secure; users, points of contact, transmission. Relative risk/impact of data loss
- Deployment of your proposed system
- Road Test: Attempt to hack your system; learn about weak spots, etc.
- Synthesis: Incorporate road test data, re-deploy
- Auditing: Periodic security monitoring, checks of system, fine-tuning
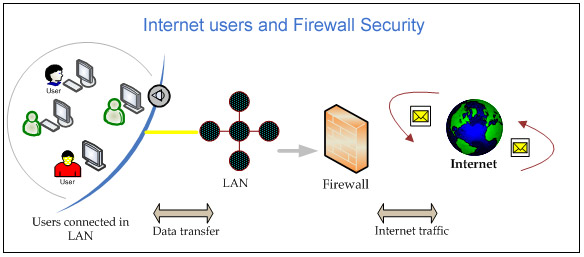
When analyzing the threats to your data an organization should look closely at two specific areas: Internal attacks and external attacks. The first and most common compromise of data comes from disgruntled employees. Knowing this, a good system manager separates all back-up data and back-up systems into a separately partitioned and secured space. The introduction of viruses and the attempted formatting of network drives is a typical internal attack behavior. By deploying employee cards that log an employee into the system and record the time, date and machine that the employee is on, a company automatically discourages these type of attacks.

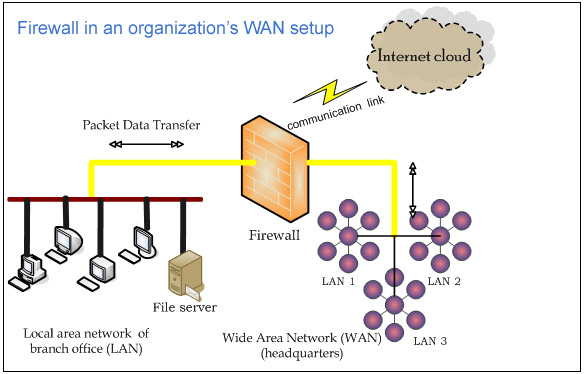
External attacks are typically aimed at the weakest link in a company's security armor. The first place an external hacker looks at is where they can intercept the transmission of your data. In a smart card-enhanced system this starts with the card.
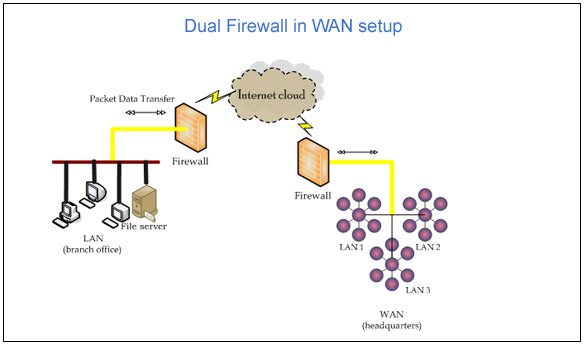
Security Architectures
When designing a system a planner should look at the total cost of ownership this includes:
- Analysis
- Installation and Deployment
- Delegated Services
- Training
- Management
- Audits and Upgrades
- Infrastructure Costs (Software and Hardware)
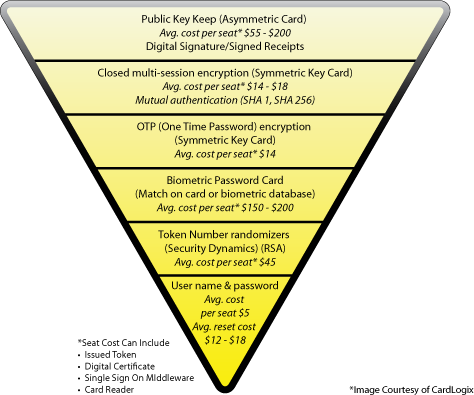
Over 99% of all U.S.- based financial networks are secured with a Private Key Infrastructure. This is changing over time, based on the sheer volume of transactions managed daily and the hassles that come with private key management. Private Key-based systems make good sense if your expected user base is less than 500,000 participants.
Public Key Systems are typically cost effective only in large volumes or where the value of data is so high that its worth the higher costs associated with this type of deployment. What most people don t realize is that Public Key systems still rely heavily on Private Key encryption for all transmission of data. The Public Key encryption algorithms are only used for non-repudiation and to secure data integrity. Public Key infrastructures as a rule employ every mechanism of data security in a nested and coordinated fashion to insure the highest level of security available today.