n this process, a perfectly ordinary piece of plaintext which can be read by anyone is converted so that it can only be read by someone with a key. One of the simplest forms of data encryption is a simple alphabetic substitution, in which the letters of the alphabet are scrambled to create a key. One could decide, for example, to shift the letters of the alphabet by five places so that “E” stands for “A,” “F” for “B” and so forth for a simple key, or the letters could be assigned at random to make a piece of text more difficult to decipher without the key.
An alphabetic substitution is usually fairly easy to break; in fact, many major newspapers have a simple substitution on their puzzles page for people to solve. More complex methods of data encryption can be used to make a code more challenging to break. With complex codes, people can try to use brute force to crack the encryption, and they may eventually succeed, but it will take a long time. Many methods of encryption focus on keeping the key secure, and allowing the encrypted data to be freely seen, under the argument that once encrypted, the data is harmless, as long as people cannot obtain the key.
There are a number of reasons to need to encrypt data, most of which rely on shielding data from the eyes of other people. Banks, for example, send encrypted data about their clients back and forth, while governments rely on encryption to get secure messages to overseas embassies. Most email programs offer data encryption while sending and receiving so that emails cannot be read by third parties, as do sites which handle personal information like addresses and credit card numbers.
Some encryption protocols are standardized so that people can easily communicate with each other, while in other cases, a key may be developed specifically for use by particular people, and the key is not standardized to make it harder to crack. Personalized keys were once the only way to encrypt data, until shared key encryption allowed people to exchange information about a key across an open network without disclosing the contents of the key itself.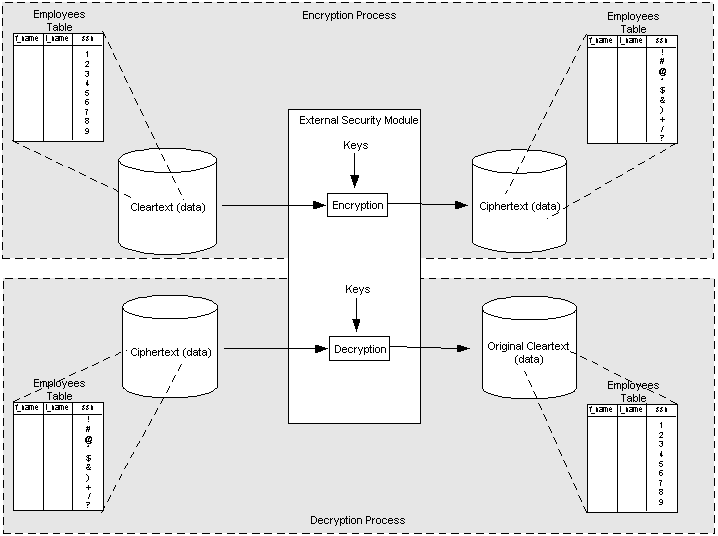
Benefits of Data Encryption
For large commercial organizations, data security is not only a corporation option, it's the law. Losing sensitive data by way of natural disasters or physical theft can have severe consequences on a company, possibly crippling the entire organization. While there are many different security mechanisms, data encryption is perhaps the most effective in regard to protecting confidential information.
Virtual attack - This could be an industry rival that learns to bypass security and gains access to competitive data. It could also be a malicious attack that purposely corrupts data.
Physical attack - Perhaps a disgruntled employee is seeking ways to damage the company by stealing files or purposely destroying data.
Most corporations implement multiple forms of security by using hardware solutions such as routers and firewalls. These devices protect essential data by keeping external threats out of the network. Unfortunately, intruders will employ numerous attacks, specifically targeted at your information. When attackers find a way to penetrate your first line of defense, data encryption steps up and helps to ensure that your secrets can't be viewed.
Encryption has changed drastically over the years, going from a military solution to widespread public use. Whether it's hardware or software-based, this method is fast, easy to use and most important, secure. Here some of the key benefits this solution offers:
Power: The best in data encryption is based on global standards, able to mitigate potential corruption without flaw. Many solutions are large enough to ensure that an entire organization is in full compliance with security policies. Data encryption allows a corporation to achieve military-level security with easy and affordable solutions.
Flexibility: Data encryption can protect your sensitive information whether it's stored on a desktop or laptop computer, a PDA, removable storage media, an email server or even the corporate network. This allows you to securely access important data from the office, on the road or at home. If the device is lost or stolen, the information will be protected by the data encryption mechanism.
Transparency: It wouldn't be a good idea to employ any security measure that negatively impacts your business. An efficient data encryption solution enables your business to flow at a normal pace, silently securing crucial data in the background. Some of the best options are those running effectively without the user even being aware.
There are many benefits of data encryption as this solution provides solid protection in the event of a security breach. Not only does it offer peace of mind, it also frees up resources normally used by your perimeter defenses. Every security measure you set in place is important yet inefficient if confidential data itself is not protected.
No comments:
Post a Comment